LockBit Developer Rostislav Panev Extradited from Israel to the US
The US extradites LockBit ransomware developer, Rostislav Panev, from Israel. Learn how his arrest impacts the fight against cybercrime and understand LockBit’s devastating impact.
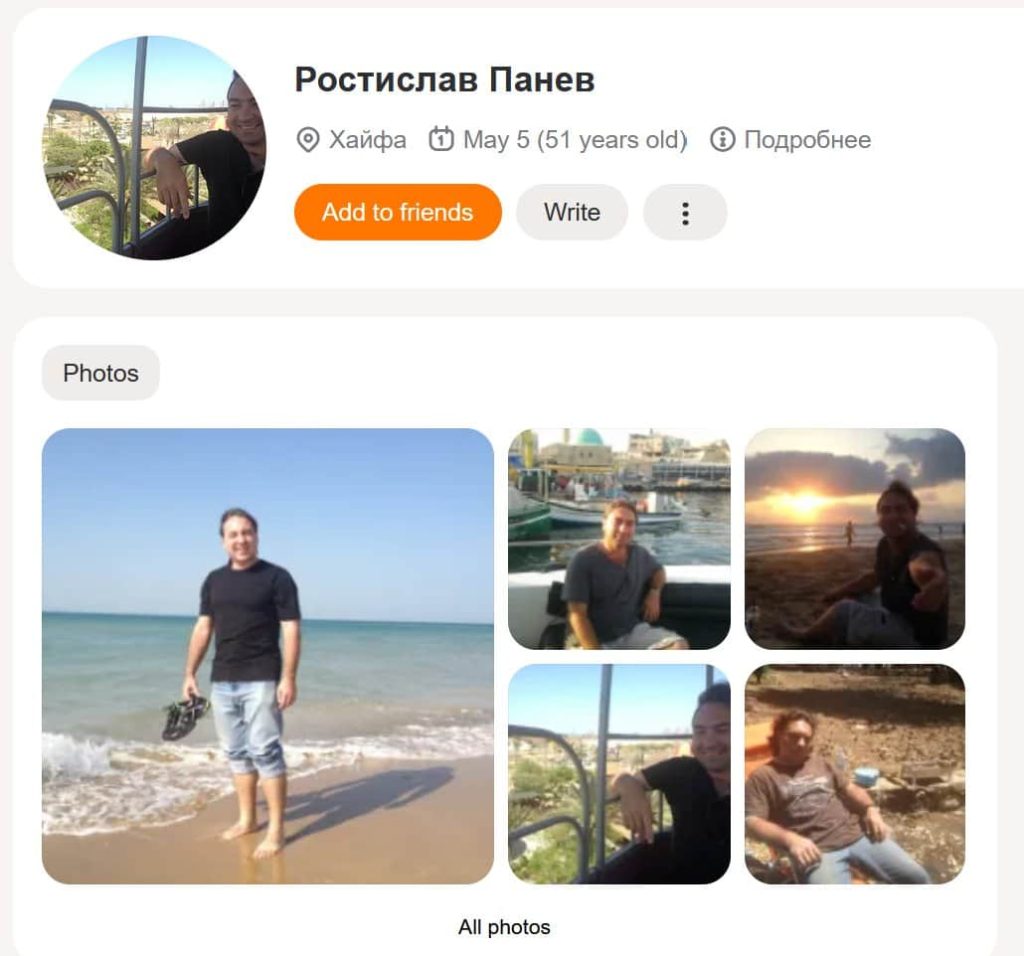
The United States has achieved a significant victory in its ongoing battle against cybercrime with the extradition of Rostislav Panev, a 51-year-old dual Russian and Israeli national, who is accused of being a key developer of the notorious LockBit ransomware.
Panev is alleged to have been deeply involved in the development and maintenance of the LockBit ransomware from its inception around 2019 until at least February 2024. During this period, he and his co-conspirators are believed to have transformed LockBit into what the Department of Justice (DoJ) describes as “the most active and destructive ransomware group in the world.”
The group, operating as a ransomware-as-a-service (RaaS) model, is believed to have targeted over 2,500 victims across at least 120 countries, including approximately 1,800 victims within the United States. These victims spanned across critical sectors, encompassing hospitals, schools, and government agencies, causing widespread disruption and financial losses.
The financial impact of LockBit’s activities is staggering. According to the DoJ, the group successfully extracted at least $500 million in ransom payments, while causing billions of dollars in additional losses through lost revenue and recovery costs. Evidence uncovered by law enforcement indicates Panev’s direct involvement in the development of tools that facilitated these attacks.
“The LockBit group attacked more than 2,500 victims in at least 120 countries around the world, including 1,800 in the United States. Their victims ranged from individuals and small businesses to multinational corporations, including hospitals, schools, nonprofit organizations, critical infrastructure, and government and law-enforcement agencies,” the DoJ’s press release revealed.
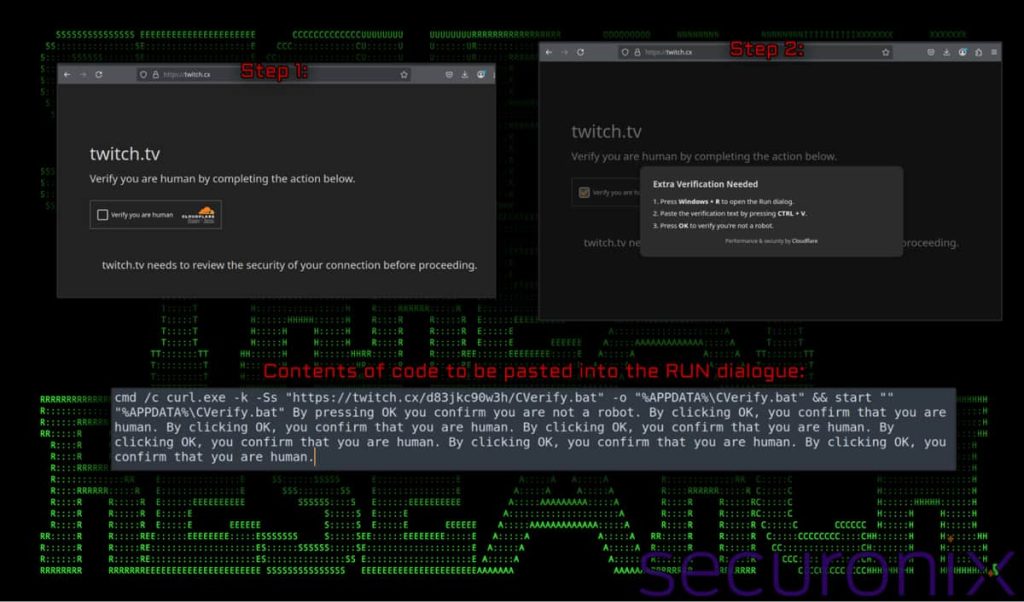
Authorities discovered administrator credentials on his computer, granting access to a dark web repository containing the source code for multiple versions of the LockBit builder, which enabled affiliates to generate custom malware.
They also found source code for the StealBit tool, used to exfiltrate stolen data, and evidence of direct communications between Panev and Dmitry Yuryevich Khoroshev, the alleged primary administrator of LockBit. They were charged by the DoJ, discussing development work on the LockBit builder and control panel.
Furthermore, financial records revealed cryptocurrency transfers exceeding $230,000 from Khoroshev to Panev between June 2022 and February 2024, providing concrete evidence of their financial relationship. In interviews with Israeli authorities, Panev reportedly admitted to performing coding, development, and consulting work for LockBit, confirming the regular cryptocurrency payments he received.
Panev’s extradition from Israel, where he was apprehended in August 2024 following a US provisional arrest request, marks a crucial step in holding individuals accountable for their roles in the devastating ransomware attacks that have plagued organizations worldwide. He has since appeared before a US magistrate and will remain detained pending his trial.
Top/Featured Image: Pixabay/Maxleron